Cybersecurity
Protect your company
from cyber attacks



Securing the entire IT infrastructure with a holistic security concept
✓ Endpoint Security
.
✓ Network Security
.
✓ Managed Threat Detection & Response
Arrange a free initial consultation!
We protect the most valuable,
you have: Your data.

Endpoint Security
Mobile devices such as laptops, smartphones and tablets & are the main targets of hackers and
malware for companies.
These so-called “endpoints” are the greatest vulnerabilities within the company. In addition to technical vulnerabilities, it is primarily the employees’ lack of knowledge in handling the devices that can lead to a potential threat situation.
Endpoint Security Management includes
areas such as:
✔ Firewall
✔ Real-time antivirus / anti-malware
✔ Secure Gateway
✔ Ai Threat Detection
✔ Mobile Device Security
Secure all endpoints in your organization. For optimal and holistic protection against all types of malware, cyberattacks and other digital threats.
Network Security
The following areas are part of a network security system:
✔ VPN
✔ Network segmentation
✔ Access control and assignment
✔ Cloud Security
✔ DLP (Data-Loss-Prevention)
✔ Incident Response
Protect your corporate network effectively against unauthorized access and malware. Prevent DDoS attacks through intelligent access allocation with individually configured firewalls, secure gateway, VPN and more.
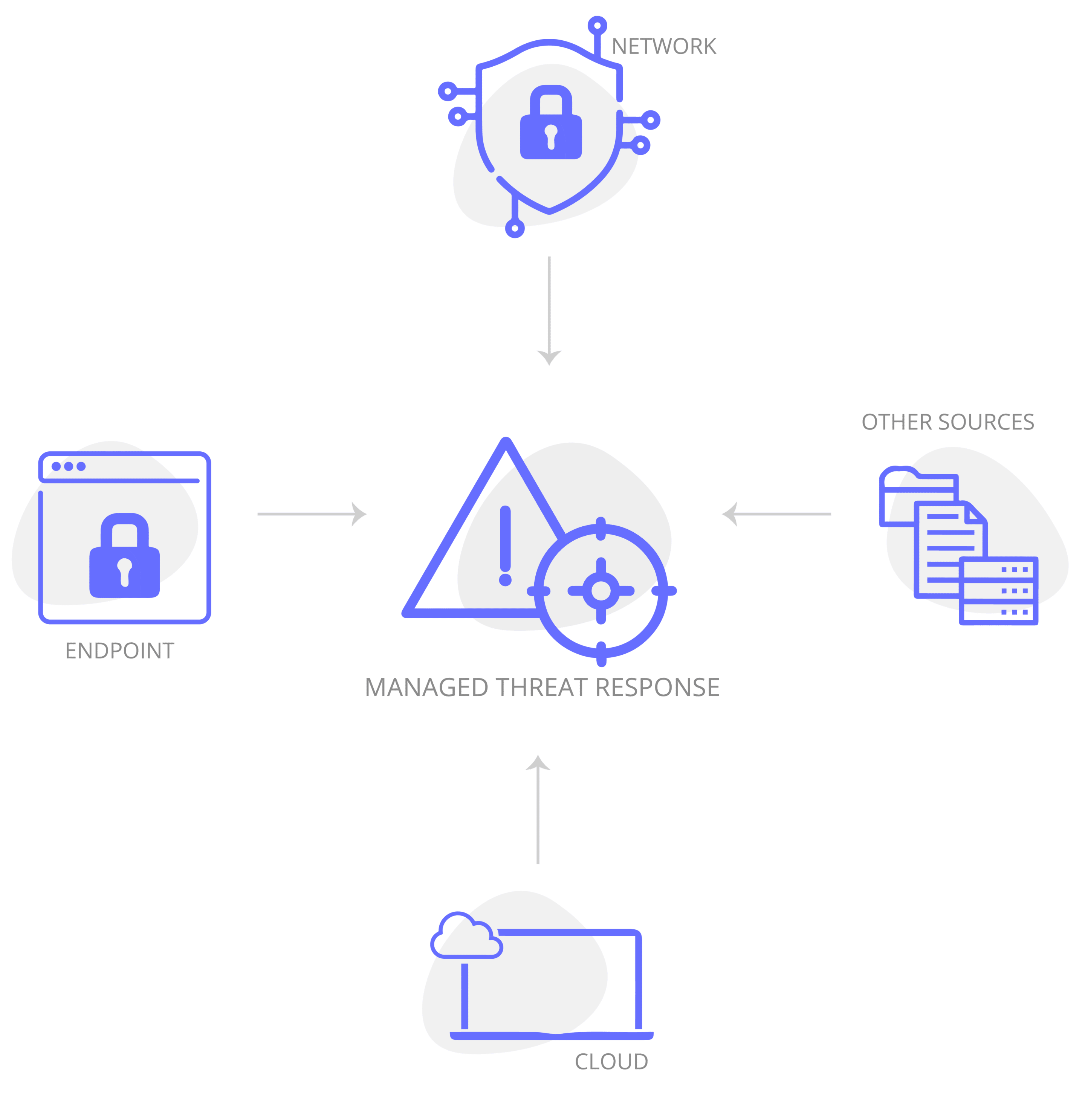
Managed Threat Response
An MTR solution helps them in the following areas:
✔ Automated endpoint detection
✔ Isolate infected endpoints from the network
✔ Wifi restrictions for unverified endpoint
✔ Identification of all apps used by users
✔ Central BackUp Management
✔ Cloud-Reporting
Accurate analysis of anomalies and suspicious files and activities on the network. Fast and effective attack remediation, back-up recovery if necessary, and damage mitigation with Managed Threat Detection and Response (MTR).
Data security and data protection
Because in addition to your data, the data of your customers and partners will probably also be stolen.
The EU GDPR provides for a notification obligation in the event of a personal data breach. In concrete terms, this means that a data leak must be reported to the authorities within 72 hours of becoming known.
With the help of jemix and SOPHOS you not only protect sensitive data of your company, but also the data of your customers.
✔ Avoid data leaks
✔ Ensure security and integrity of corporate data
✔ Maintain DSGVO compliance
Microsoft 365 Security
Protect your Microsoft 365 environment: For maximum security of Teams, Outlook and Co. Full protection for Microsoft’s cloud services with the IT experts from jemix.


Have we sparked your interest?
Get in touch with us!
Contact us